Electronic Warfare is here to stay
Cyber warfare has numerous attack methods with which the enemy can be effectively targeted
image for illustrative purpose
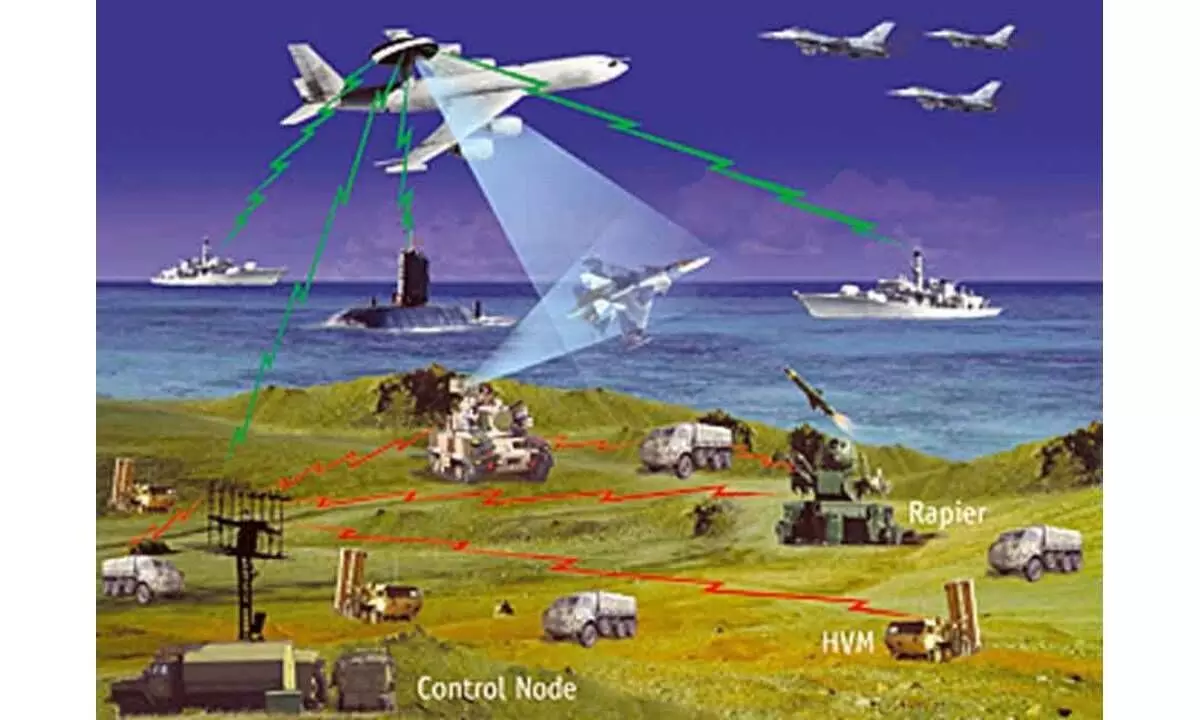
Electronic warfare (EW) is a mature sector, but still has substantial room to grow in both volume and technological capability. With the so-called 'revolution in military affairs’, the proliferation of precision weapons and advanced communications and the armed forces relying on systems vulnerable to electronic warfare has grown significantly.
Electronic warfare (EW) detects, interprets, controls or disrupts signals in the electromagnetic (EM) spectrum, typically radar, radio or infrared transmissions, to protect military assets from potential threats.
Modern military capabilities rely increasingly on the electromagnetic spectrum. War fighters depend on the spectrum to communicate with each other and their commanders, to understand the environment and inform decisions, to accurately identify and engage targets, and to protect them from harm.
Control of the electromagnetic spectrum is critical in modern warfare, as it is used for weapons guidance, allied communication and enemy identification and suppression.
According to our latest study, the global Electronic Warfare Systems market size was valued at $16,740 million in 2022 and is forecast to a readjusted size of $22,060 million by 2029 with a CAGR of 4.0 (percent) during review period. The influence of Covid-19 and the Russia-Ukraine War were taken into consideration while estimating market sizes.
North America is forecast to hold the largest share in the market due to rising insurgencies, territorial disputes, terrorism, and the unrest in other nations, thus driving the global market upwards till 2026.
Russia, China, North Korea and Iran are involved in the act of modernizing their EW equipment in a bid to hold a better share in the market. Acts like these will help foster the growth of the market over the forecasted period. Cyber warfare is not static and has various attack methods, which can be used to target an enemy.
A few of the most popular trends within it:
Ransomware attacks are some of the most disruptive attacks globally, with cybercriminals encrypting data unless a payment is made. These attacks become even more dangerous in cyber warfare as usually there is no financial motive and the intention is to cause as much damage as possible to the enemy’s ability to operate. In addition to ransomware, cyber cells of nation-states can exploit zero-day attacks to inject malware into the enemy’s systems. These can be used for various reasons, ranging from sabotage to espionage.
Distributed Denial of Service (DDOS) attacks: DDOS attacks can be devastating in their ability to stop the operations of critical companies and governments. By targeting essential government functions and infrastructure such as the power and water grid, attackers can bring the society to a grinding to a halt while public confidence in their leaders will take a major beating.
Supply chain attacks: Supply chains can be a dangerous blind spot in most cyber defence. Attackers can target governments and companies’ software or physical supply chains to inject malicious code that can be activated later. Or the entire supply chain can be disrupted to cause operations to stop.
Cyber warfare is the next evolution of electronic warfare, which is seemingly here to stay. Attacks and techniques will only get further advanced with time, and governments and companies must update themselves to ensure they are protected.
A few of the critical technical and non-technical measures that can be taken include the governments dispersing their key digital assets and not centralize them where a physical or digital attack can take them out. Taking advantage of technologies like the public cloud enables governments to host their assets in multiple data centres and not have a single point of failure.
They must ensure that best technical practices like strong passwords, multi-factor authentication, patching, firewalls, anti-malware and security scanning are all implemented. An integration of these can help build a robust security layer against cyber warfare. It is especially critical to ensure that systems and applications remain patched so that they are able to withstand malware and other attacks.
A comprehensive backup strategy should be implemented to cover key data in case of a physical or cyberattack. It is especially critical to ensure there is an air gap between backup copies so that attacks like ransomware cannot infect all copies of a backup. Periodic assessments and red teaming exercises must be carried out to identify weak pots before they can be exploited in wartime. Information shared via threat intelligence feeds should immediately be incorporated and used in these tests so that they remain relevant. Employee training is crucial at times of cyber warfare. Usually, employees and the general public are targeted by cyberattacks to gain an initial foothold. Along with regular security training of employees, the general public should also be educated against misinformation.
Combatants are actively using cyberattacks to harm and impair the enemy’s digital capabilities as a crucial strategic advantage both on and off the battlefield.

